Introducing runtime detection and isolation for Lambda and EC2

Today, we’re excited to publicly announce a first of its kind, unified, identity-driven detection and isolation capability for your cloud-native and cloud-enabled apps and infrastructure. More specifically, our approach unifies data provided by AWS with purpose-built identity-driven context and introspection for Lambda and EC2.
We launched ClearVector with the idea of making an adversary’s job extremely difficult. That's why we're on a mission to enable realtime intelligence and control over the identities operating in an environment. Having an agentless or API-only solution isn’t enough to accomplish this; you need to prevent the adversary at runtime, across all layers of your environment.
To be clear – we believe in endpoint agents and have extensive experience building and deploying these solutions at scale. Without instrumentation tailored to your workload, you do not have the visibility or capability to prevent or isolate identities, activity, or stop the adversary. Software that scans using cloud provider APIs cannot protect you from an attack as it happens – by definition they are outside the OODA loop of the adversary. From the beginning of ClearVector, we designed a modular architecture to do more than stop identities and activity at the infrastructure layer; we are built to protect other layers, such as EC2 and serverless, using our unified, identity-driven platform. Furthermore, our endpoint capabilities are designed specifically to address problems unique to production environments.
From our experience protecting large cloud environments at scale, there are significant differences when compared to a traditional IT environment. In production environments, you need purpose-built capabilities that at a minimum have a predictable footprint in both CPU and memory – this is different than the way endpoint software is built and architected for traditional IT environments, such as employee laptops.
Now, we've extended our identity-driven platform into both Lambda and EC2. This unprecedented view across traditional production endpoints, serverless endpoints and the infrastructure layer, at runtime and in near realtime – combined with our identity-driven approach – enables extremely fast, unified detection and isolation of risky identities and adversaries.
The case of stolen developer credentials
For example, there have been multiple attacks where an adversary compromises a developer workstation, steals AWS credentials, uses these credentials to log in to production, spins up and SSHs into an EC2 system, and moves laterally in the environment to achieve their mission.
In Figure 1, we show how ClearVector detects this attack and notifies you:
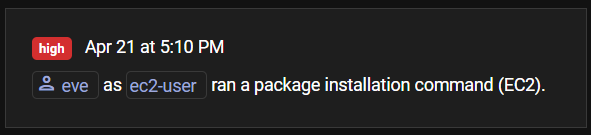
When pivoting back into the console from the Slack or Teams notification, our CloudDVR displays on a single timeline and screen what “eve” has been doing in the environment. If needed, you can quickly pivot through our patented, purpose-built graph to more deeply understand the risk.
In addition, Figure 2 shows how you can quickly see the commands run by the adversary on the EC2 instance, threaded together with the relevant infrastructure activity.
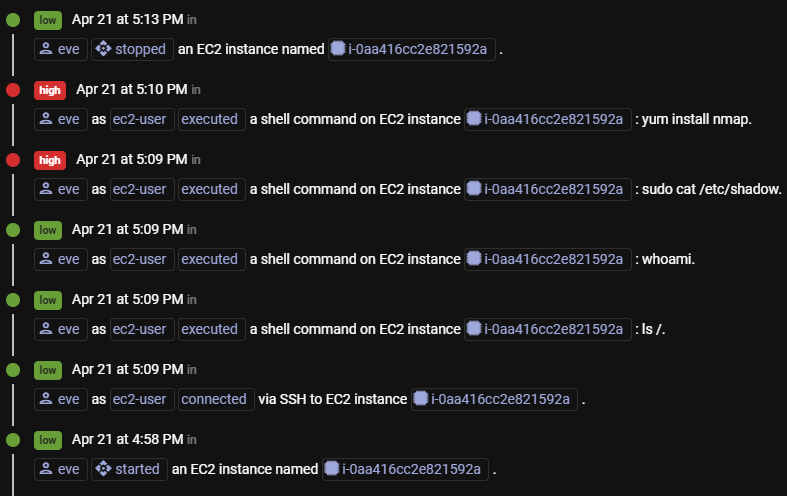
Finally, you can isolate “eve” across both the infrastructure layer and the EC2 layer, further preventing any future damage, as shown in Figure 3:
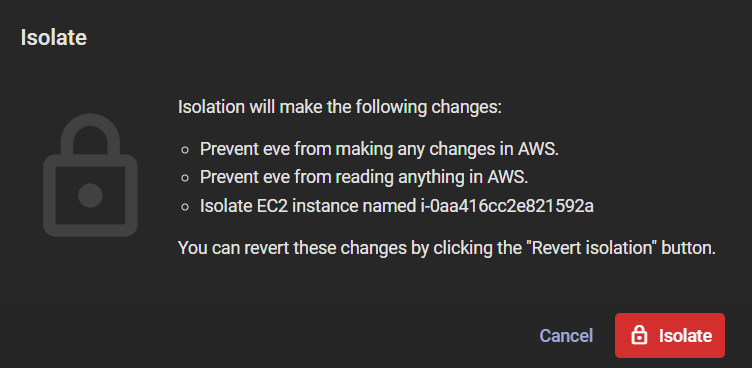
Stay tuned for a future post highlighting a scenario with Lambda!
Existing ClearVector customers can opt-in to our technical preview to gain access to these capabilities. Check us out at fwd:cloudsec next week or contact us directly to learn more!

